A data breach creates the worst possible options that leave your data security broken and your company’s private information available to outsiders. As the age of the digital world begins expanding, so do the criminals and their options to make use of private data.
Cybersecurity with advanced technology can easily prevent any illegal attempts by criminals. However, there are always risks, even with all the protection you have utilized to ensure the safety of your company’s information.
Regardless of whether you have enhanced cybersecurity or not, what do you do if the worst-case scenario happens? In other words, what to do if your data has been breached?
Panicking is a natural response to something you lose control of. To keep the risks isolated and your company less damaged, taking steps and taking back control is necessary, especially when it comes to something unforeseen like a data breach.
What is a Data Breach?
The definition of a data breach is when private information is taken without any authorisation by an unknown user. The worst part about a data breach is when the company employees and founders don’t recognise that their data has been exposed.
You can identify suspicious activity to investigate whether or not your data is compromised. The key is to have consistent maintenance, organised reports, and monitoring. This is because you can find unnatural behaviours to identify a breach.
What Data Might Be Exposed?
Exposed data can be used for many illegal activities such as identity theft, ransom, and sensitive credit card information of customers. Cybercriminals can also take advantage of the trade secrets, private medical records, or financial information of the company and its members.
The most dangerous part of a data breach, aside from using credit card numbers and identity theft, would be illegally stealing national security documents if the company works for government departments.
Effects of Data Breach
Aside from the potential stealing of documents, the aftereffects create a gap in your company’s structure that weakens it entirely. There are 4 consequences of a data breach for a company. What it does to the morale, reputation, and capital of a brand can be fatal.
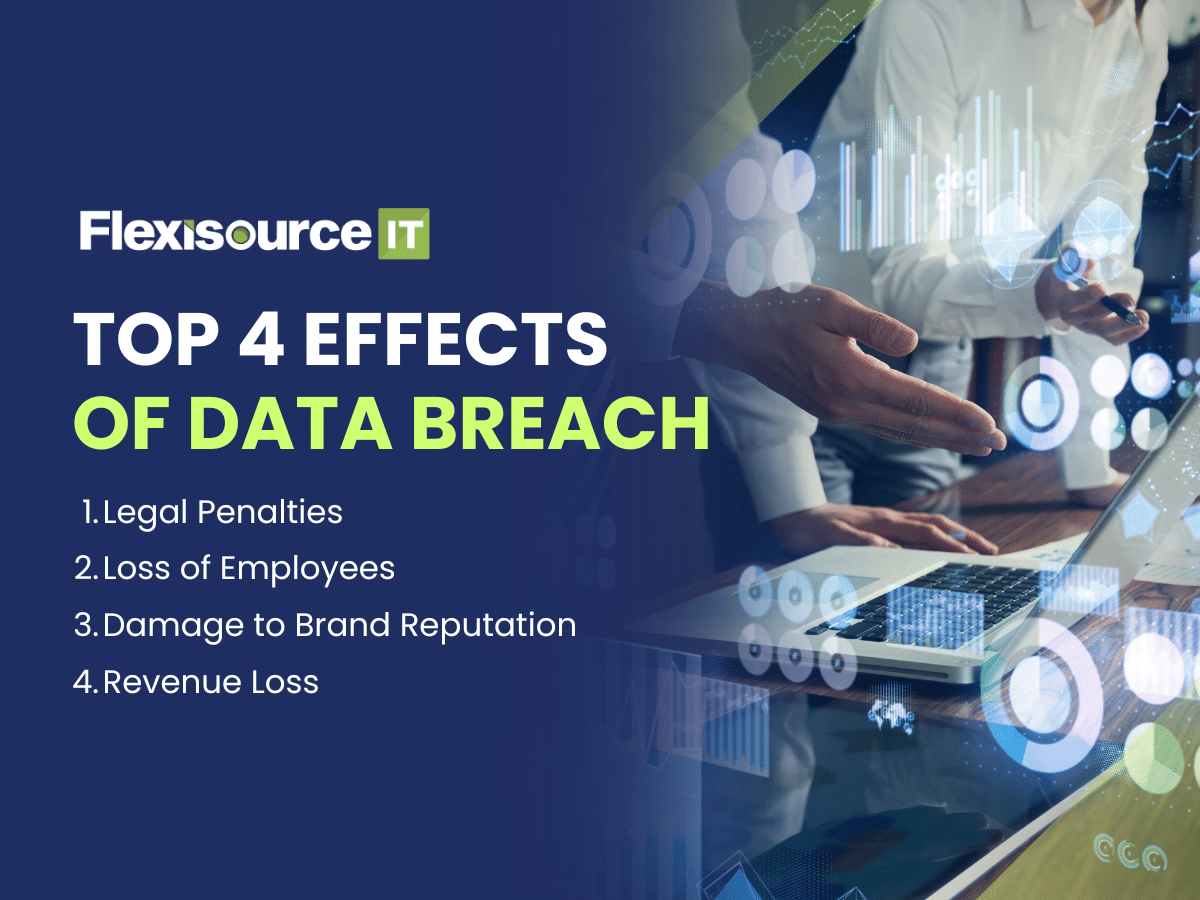
Legal Penalties
The biggest problem will be the legal penalties your company is liable for. Fines can lead up to billions of dollars depending on how much impact and information was stolen by the cybercriminals. The higher the risk of information taken, the higher the fines.
It doesn’t just end there. Depending on the trial your company will face, your customers will also receive compensation for the loss of their private information due to the breach.
An example of this would be Equifax in 2019, who experienced a breach and was fined 700 million dollars. It was a cause of uproar then, with consumers of the brand and the public outraged after learning the breach occurred for months while the company itself didn’t even notice.
Loss of Employees
There are also consequences of a data breach for an employee. Because of an ensuing panic and historical events, insider threats can create doubt within the company. Employees will feel the pressure of trying to prove their innocence and distrust will spread between one another.
This results in an unhealthy environment wherein many employees will choose to leave the company. Hiring new employees just recently after a breach will prove difficult, adding more pressure and stress to those who stayed as they pick up the empty slacks of those who left.
Damage to Brand Reputation
The impact of a data breach on individuals who placed their trust in your brand and were affected can erase all trust built up. If a person learns that their disclosed information has been leaked and used maliciously, it is only natural that said person would lose faith in the company that promised to safeguard their information.
The damages to your brand’s reputation will be severe if not handled properly. If the criminals manage to get the information of numerous individuals, there is a certain guarantee that the breach itself will reach the public. This creates an image of dubious security for your brand.
Such negative effects on a brand’s reputation can cause loss of customers and employees. Potential customers will also lose interest in even inquiring about your brand for fear of its flimsy security.
Revenue Loss
Regardless of whether or not your company handled the breach well, revenue loss is to be expected. Locking in and resolving the breach, facing any potential penalties, and all the other risk mitigation instructions will still require a stop to specific functions of your business.
By doing so the company either proceeds slowly in processing their business or halts it altogether until the matter is resolved. In worst-case scenarios, uncoordinated solving of a breach can create giant losses in revenue and even higher debt in terms of penalties and compensations.
Steps to Take After a Data Breach
In the digital age, there will always be cyber threats. While cybersecurity helps a company protect itself, many tend to overlook what a company should do after a data breach. Listed below are preparations to protect yourself and your company should enhanced cybersecurity still fail.
Create and Implement an Incident Response Plan
The first step after a data breach is to follow an incident response plan (IRP). Creating an incident response plan and briefing the employees on what to do in such cases can make collaboration to prevent more damage from a breach.
Incident response plans vary depending on what companies decide or prioritise. However, it is necessary to alert cybersecurity specialists and IT teams immediately to find a solution together. Furthermore, alerting all employees and announcing the breach may induce panic without a proper meeting that teaches them what to do and what not to do.
Isolate Breach Location
Now that you have all the staff prepared and taking the necessary steps to mitigate the damage of the data breach, it’s time to isolate it. Thanks to the help of your IT team or cybersecurity specialist, you can pinpoint the entry of the breach.
If the breach came from an account, simply restrict its permissions and follow the advice of your IT professionals on how to handle the account. It’s also important to check in on your code structure. Keep in mind that there may either be extensive or minimal damage to the specific code they’ve manipulated that can affect the rest of your code’s functions.
Minimise the damage as much as possible. Disengage the affected areas and isolate them to prevent the cybercriminal from gaining more control.
Collect and Keep Evidence
Collecting evidence and damage reports is necessary for the investigation on the cause of the data breach. It’s also another reason why all employees should be aware of the protocols necessary during an attack.
Accounts with mismatched information, non-functioning codes, and other manipulated data should be listed. Any contact with the cybercriminals should also be taken in, recorded, and kept as evidence.
Team Collaboration and Communication
Collaboration and communication are crucial during challenging times like a data breach. Ensure that your protocols highlight that employees must wait for the company itself to announce the breach first to prevent further damage to the brand’s reputation.
Furthermore, no help is too big or too small. Every available information and aid your employees can do to limit the damages, from interacting with customers to refixing the damaged data, is greatly appreciated.
Make sure that each member is fully aware of the actions of each other to prevent further confusion and proceed with mediating your data’s security more efficiently.
Transparency with Customers
While standing on a united front during a data breach is admirable, it’s only a matter of time until customers notice irregularities within your brand. It’s best to immediately explain the damages caused by an illegal breach made without the company’s consent to customers as soon as possible.
Many Internet users know how to check if personal information has been compromised. Should they find out ahead of your announcement the possibility of losing their trust, increasing negative brand reputation, and losing customers is high.
Incident Report to Police
Avoiding penalties by hiding information or even the event of your company’s data breach will only increase fines and compensation. Furthermore, your country’s government may know the perpetrator behind the cyberattacks.
There are many data protection tips regarding interacting with cyber criminals and collaborating with the police to retrieve data. Advanced cybersecurity specialists may be able to locate where the criminals plan to sell the information they’ve taken from you while the police can investigate further and identify them.
Review Statements of Breach with Employees
Every employee must have the same statements regarding the data breach. This means holding a meeting regarding the event and discussing the heart of the issue while explaining how the breach came to be.
It also involves explaining to the employees what the company has done to prevent the damage from spreading further and their necessary planned steps to enhance cybersecurity.
By doing so, employees can refrain from spreading conflicting reports that stir doubt amongst the public regarding your brand’s trustworthiness.
Conclusion
Data breach is a serious thing to deal with and the way a company handles it can make or break its future. While these steps and tips can help you spot and deal with the near-fatal data breaches you may experience, prevention is always better than a cure.
Protect your data by hiring specialists advanced in cybersecurity and daily maintenance to ensure your company and clients are safe from cybercriminals. While it may be too expensive to hire an in-house cybersecurity team, hybrid outsourcing companies like Flexisource IT can support your brand and offer risk mitigation solutions!